What is two-factor authentication and how can it make your business more secure?

In this article, we delve deeper into the concept of two-factor authentication, providing you with comprehensive insights on how it can effectively enhance security measures for both you and your customers.
Businesses are always looking for new ways to improve security for their customers.
“Hacker anxiety” is top of mind for many customers, with 75% believing they could fall vulnerable to cyberattacks. These concerns can have huge repercussions for businesses—with 81% of consumers stating they’d stop engaging with a brand following a large data breach.
From banks to Google’s Gmail, more and more businesses are using two-factor authentication to help alleviate customer anxiety and better protect their accounts and data. Research shows that multi-factor authentication, of which two-factor authentication (2FA) is one of the most popular, can block up to 99.9% of automated cyberattacks.
In this post, we explore two-factor authentication in more detail and show you how you can use it to increase security for you and your customers.
What is two-factor authentication?
Two-factor authentication is an electronic authentication method that requests two forms of authentication from customers to help protect their accounts or data. To help provide an added layer of security, 2FA relies on any two of the three following pieces of authentication:
- Something you know: requests something that customers know, like a one-time pin code sent to their phone or a password
- Something you possess: depends on something a consumer owns, like a bank card or mobile
- Something you are: relies on something a customer physically possesses, such as iPhone’s face scan authentication feature
2FA goes a step further than the common two-step authentication approach that typically relies on two knowledge factors, such as two different passwords or the answer to a security question based on personal details.
How does 2FA increase security?
81% of hacking-driven breaches are down to weak or stolen passwords. Rather than relying on passwords that are easily guessed, leaked, or stolen, 2FA relies on more than just internal knowledge to keep your customers safe.
Unlike passwords, possession factors are hard to access. Even if someone stole a phone, they still wouldn’t be able to provide a fingerprint replica or guess a complex password to access customers’ accounts or data.
You can use 2FA to help verify suspicious account log-ins. For example, you can use 2FA to verify account holders logging in from a new location or device.
Help prevent fraud
Payment fraud has tripled since 2011, with stolen amounts set to hit $49 billion by 2030. More and more businesses are using one-time passcodes to verify payment transactions, providing an additional level of security to their customers.
Luckily, 2FA is claimed to be one of the most effective security practices for helping to prevent payment fraud. You can also use 2FA to verify payment transactions for customers using online payment processors, credit cards, and third-party payment providers to make purchases.
How does 2FA work?
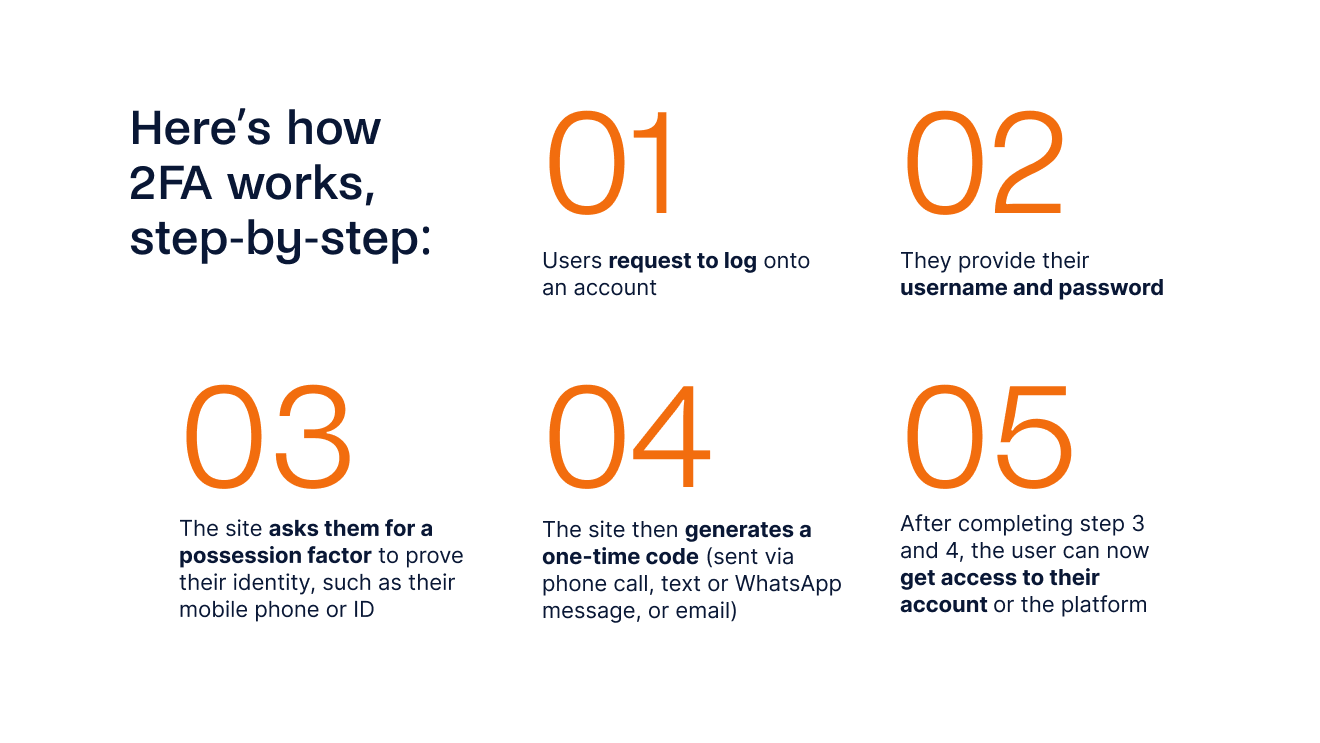
Here’s a step-by-step breakdown of how 2FA works:
- Users request to log onto an account
- They provide their username and password
- The site asks them for a possession factor to prove their identity, such as their mobile phone or ID
- The site then generates a one-time code (sent via phone call, SMS, [SB3] [KL4] or WhatsApp message, or email)
- After completing step 3 and 4, the user can now access their account or the platform
Which channels can you use 2FA on?
When it comes to successfully deploying 2FA, it’s all about balancing security with usability. Which channels are the most secure? Which provides the most seamless, hassle-free experience for your users?
Here are some of the most popular channels to choose from:
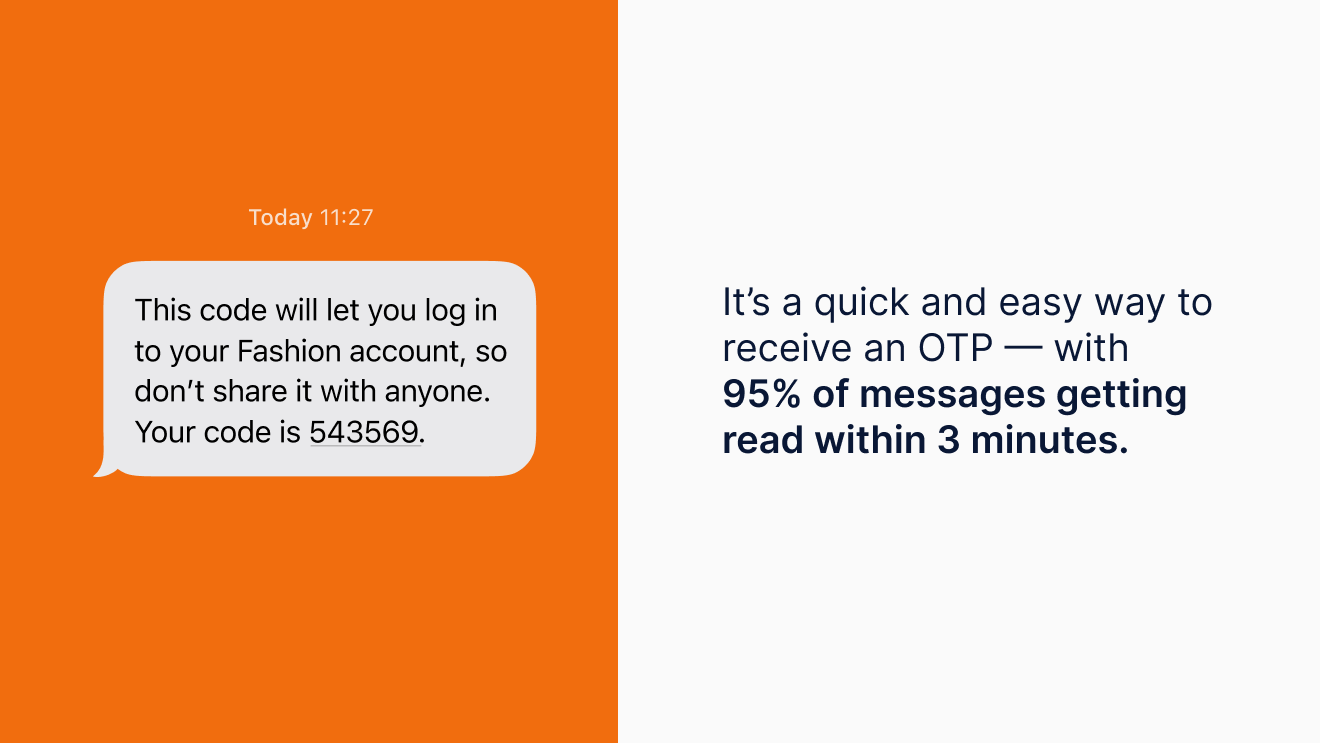
- SMS
SMS is one of the most common channels companies use to send users a one-time passcode (OTP). It’s a quick and easy way to receive an OTP—with 95% of messages getting read within 3 minutes.
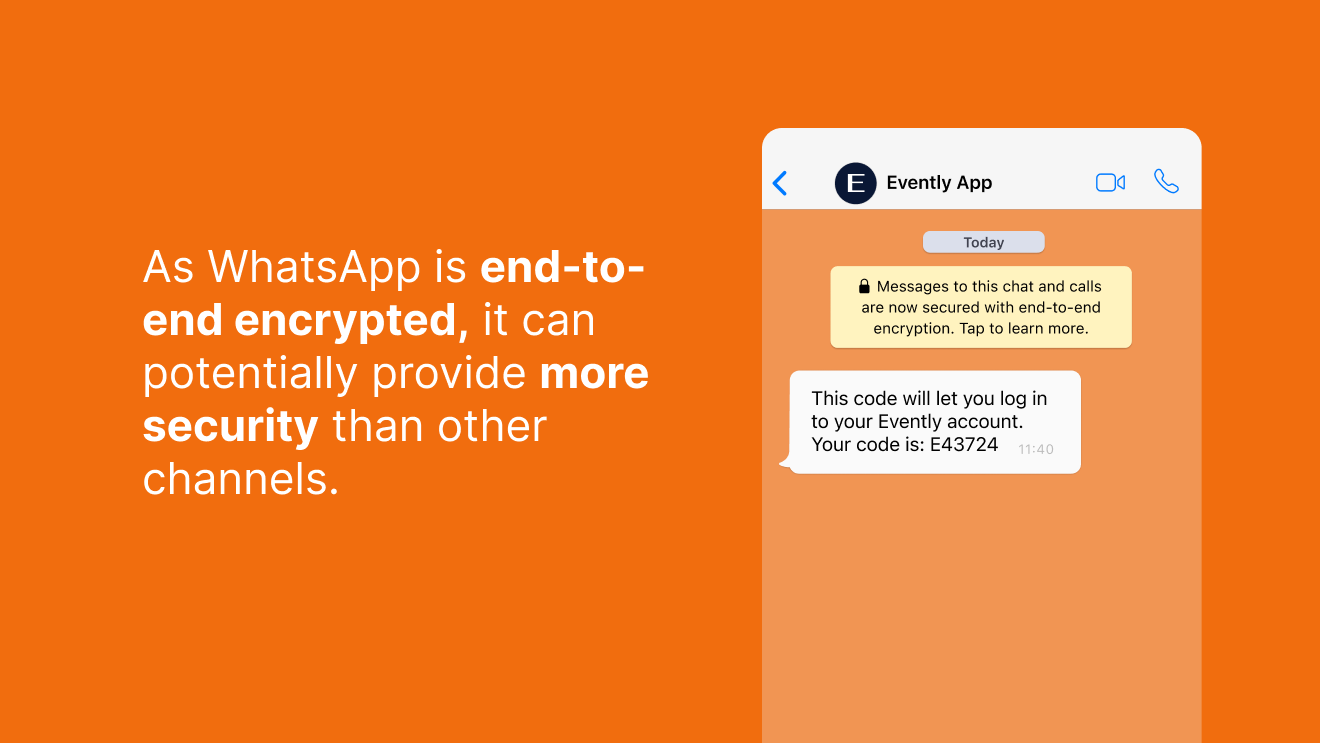
More than one in five people around the world use WhatsApp—making it more popular than SMS across Europe.
As WhatsApp is end-to-end encrypted, it can potentially provide more security than other channels when it comes to sending one-time passcodes.
- Authentication applications
Users can also use mobile apps to generate a login code. While these may be vulnerable if a user’s phone is stolen, they can be a fast and easy way to generate a code.
- Voice
Voice-based 2FA automates a call to a user and shares a code by voice. Voice boasts great usability, as people don’t have to switch to a different app or head to their email to retrieve a code.
By integrating the tyntec 2FA API, you can hand over the 2FA process to us. Our API uses intelligent routing and direction connections to mobile operators to automate 2FA code shares via email or SMS.
Instead of a complicated multistep workflow, tyntec provides 2FA user-friendly authentication via voice and SMS. With tyntec, users’ flow isn’t interrupted, they can stay on the app or site they’re using and enter their verification code.
Boosting security with 2FA verification
With passwords so easily guessed and accounts often hacked, 2FA is one of the most effective ways to enhance security for both payment transactions and user accounts.
From SMS to authentication apps, there are a host of 2FA channels to choose from. By setting yourself up with a 2FA API, you can help provide a seamless authentication experience to users and reduce your workload.
Ready to step up your security with tyntec’s 2FA API? Find out more here.